Published: November 15, 2024
Our new bulletin Cyber Threat Watch has been created to help small businesses stay up to date on the latest threats, news, and events affecting their business. The content has been curated to make cybersecurity easy and accessible for both technical and nontechnical readers.
Featured Cyber News — Zero Trust Architecture (ZTA)

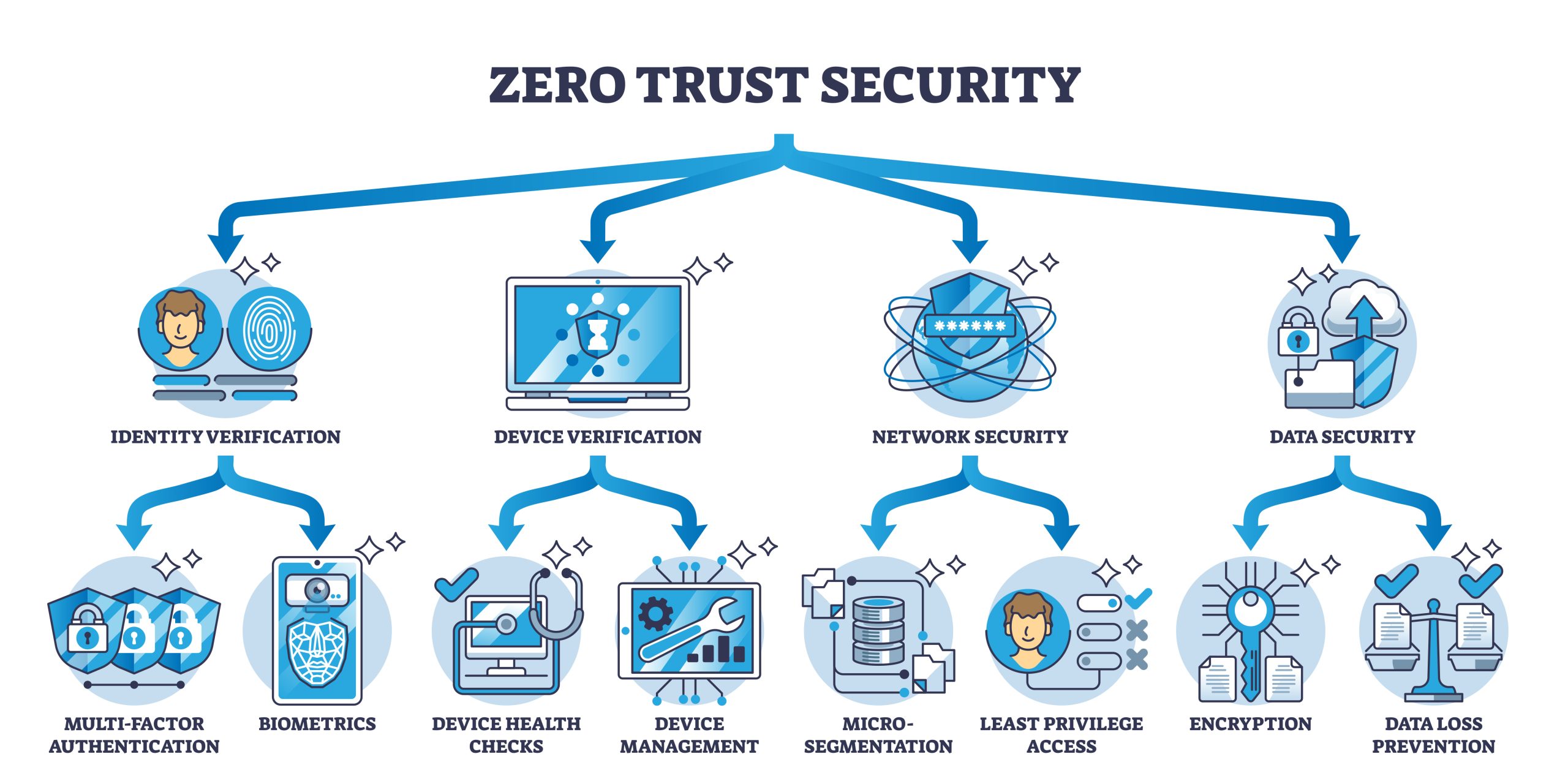
Zero Trust Architecture (ZTA) has emerged as a crucial cybersecurity approach to combat the growing threats small businesses face every day. By operating on the principle of “never trust, always verify,” ZTA ensures that every access request—whether inside or outside the network—undergoes strict verification processes.
What Is ZTA?
ZTA assumes that no entity, internal or external, can be trusted by default. It requires strict identity verification for every user and device by emphasizing authentication, access control, and real-time monitoring. The following are key components:
- Identity Verification: Ensuring that all users and devices are authenticated before accessing resources.
- Least Privilege Access: Reducing risk exposure by providing users only the access they need.
- Microsegmentation: Dividing the network into smaller, isolated segments to prevent attacks from spreading.
- Continuous Monitoring: Tracking activities constantly to identify anomalies.
Pros & Cons of Implementing ZTA
The implementation of ZTA comes with the following benefits and potential drawbacks that businesses need to be aware of.
Pros:
- Increased Security: Continuous verification reduces the risk of unauthorized access.
- Minimized Attack Surface: Least privilege limits user access to reduce the areas of vulnerabilities.
- Early Threat Detection: Real-time monitoring helps detect and respond to threats quickly.
Cons:
- Initial Complexity: Implementing ZTA can seem overwhelming, especially for businesses without dedicated IT teams.
- Potential Costs: Depending on the solutions currently used, implementing ZTA may incur additional expenses.
Affordable Strategies for Small Businesses
Even with limited budgets, there are cost-effective and accessible ways that small businesses can adopt ZTA as follows:
- Leverage Existing Tools: Start by adapting your tools already in use like firewalls, virtual private networks (VPNs), and other security software to align with ZTA. Reconfiguring your existing tools can save the cost of purchasing new programs.
- Use Multi-Factor Authentication (MFA): MFA is a simple, affordable way to enhance security by requiring multiple verification methods and reducing the risk of your accounts getting compromised. It’s often inexpensive or free, making it an effective first step.
- Start Small and Scale Gradually: Focus your ZTA efforts on first protecting the most critical assets like customer data and financial records. Expanding ZTA over time helps avoid overwhelming costs.
- Adopt Cloud-Based Solutions: Many cloud services offer built-in ZTA features, such as access control management and data encryption. They are typically more affordable than on-premises solutions and allow your business to scale security needs over time.
Getting Started with ZTA
Adopting ZTA doesn’t have to be daunting for small businesses. Here’s how your business can start:
- Assess Your Current Setup: Assess your existing tools and determine which ones can be adapted for ZTA.
- Establish a Policy: Draft guidelines for identity verification, access control, and monitoring that reflect ZTA principles.
- Test and Adjust: Run pilot projects focusing on high-priority areas to ensure that ZTA doesn’t disrupt your daily business operations.
- Educate Staff: Train employees on the importance of verifying access requests and following security best practices.
Breaking the implementation process into smaller, manageable steps can help secure your data without overwhelming the resources.
Conclusion
ZTA offers a significant boost to any business’s cybersecurity strategy. While the implementation may seem complex, the principles of ZTA can be applied gradually and cost-effectively by breaking it down into manageable steps, leveraging existing resources, and focusing on critical areas first. In this way, small businesses can enhance a resilient security posture and ensure long-term protection from evolving cyber threats.
The NCSS encourages businesses to adopt comprehensive security practices and stay informed about evolving technology trends. We recommend you consider becoming an NCSS member to access a wide range of our services. For more information, visit our Small Business page.

About the NCSS
The National Cybersecurity Society (NCSS) is committed to improving the online safety and security of the small business community through education, awareness, and advocacy. As a 501(3)(c) organization, the NCSS uses funds from charitable donations and grants to develop educational materials, webinars, weekly cyber tips, videos, and how-to-guides. The organization’s goal is to enable and empower small and medium businesses to obtain cybersecurity services, assist them in understanding their cyber risk, and advise on the type of protection needed. We want to continue to grow our community and encourage you to tell other small businesses we are here to help.
The NCSS is committed to respecting the use of images in our communication efforts. Accordingly, unless otherwise specifically noted, the graphics in our bulletin are sourced under license from Adobe Stock. The header and footer images were designed and purchased through a contract with Eyedea Advertising & Design Studio.
