Published: October 25, 2024
Our new bulletin Cyber Threat Watch has been created to help small businesses stay up to date on the latest threats, news, and events affecting their business. The content has been curated to make cybersecurity easy and accessible for both technical and nontechnical readers.
Featured Cyber Threat — Virtual Private Network (VPN) Security

As businesses increasingly rely on technology for their day-to-day operations, secure communication and data protection have become top priorities. A VPN has emerged as one of the essential tools for safeguarding online activities, especially with the rise of remote work. However, the surge in VPN usage has also led to an increase in vulnerabilities and security incidents. Therefore, understanding these challenges and implementing effective risk mitigation strategies are crucial for protecting your business.
What is a VPN?
A VPN is a technology that provides a secure, encrypted connection between your device and a server. This connection masks your IP address and makes it appear as if your online activity originates from a different server. Thus, it protects your privacy while allowing access to restricted content—it is vital for maintaining the confidentiality of sensitive data, especially when employees access the company’s networks remotely.
Understanding VPN Security Risks
The assumption that VPNs are always secure could lead to a false sense of security and increased risk for your business. Recent security incidents have highlighted several vulnerabilities in VPNs as follows:
- Endpoint Security: Devices connecting to the VPN must comply with security policies. Insecure endpoints can be entry points for attackers. For instance, cyber attackers may compromise a VPN connection through an infected employee device to gain access to the corporate network.
- Misconfiguration: Inappropriate VPN configurations can create security gaps, such as using default settings or weak authentication methods.
- Unpatched Software: Regularly updates to VPN software are essential as unpatched systems can be vulnerable to known exploits.
- Inadequate User Authentication: Weak user authentication practices, such as relying solely on usernames and passwords, increase the risk of unauthorized access.
- Outdated Encryption Protocols: Some VPNs use outdated or weak encryption methods, making them susceptible to cyberattacks. For instance, outdated protocols like Point-to-Point Tunneling Protocol (PPTP) have been known to be vulnerable to several types of attacks, such as brute force and man-in-the-middle attacks.
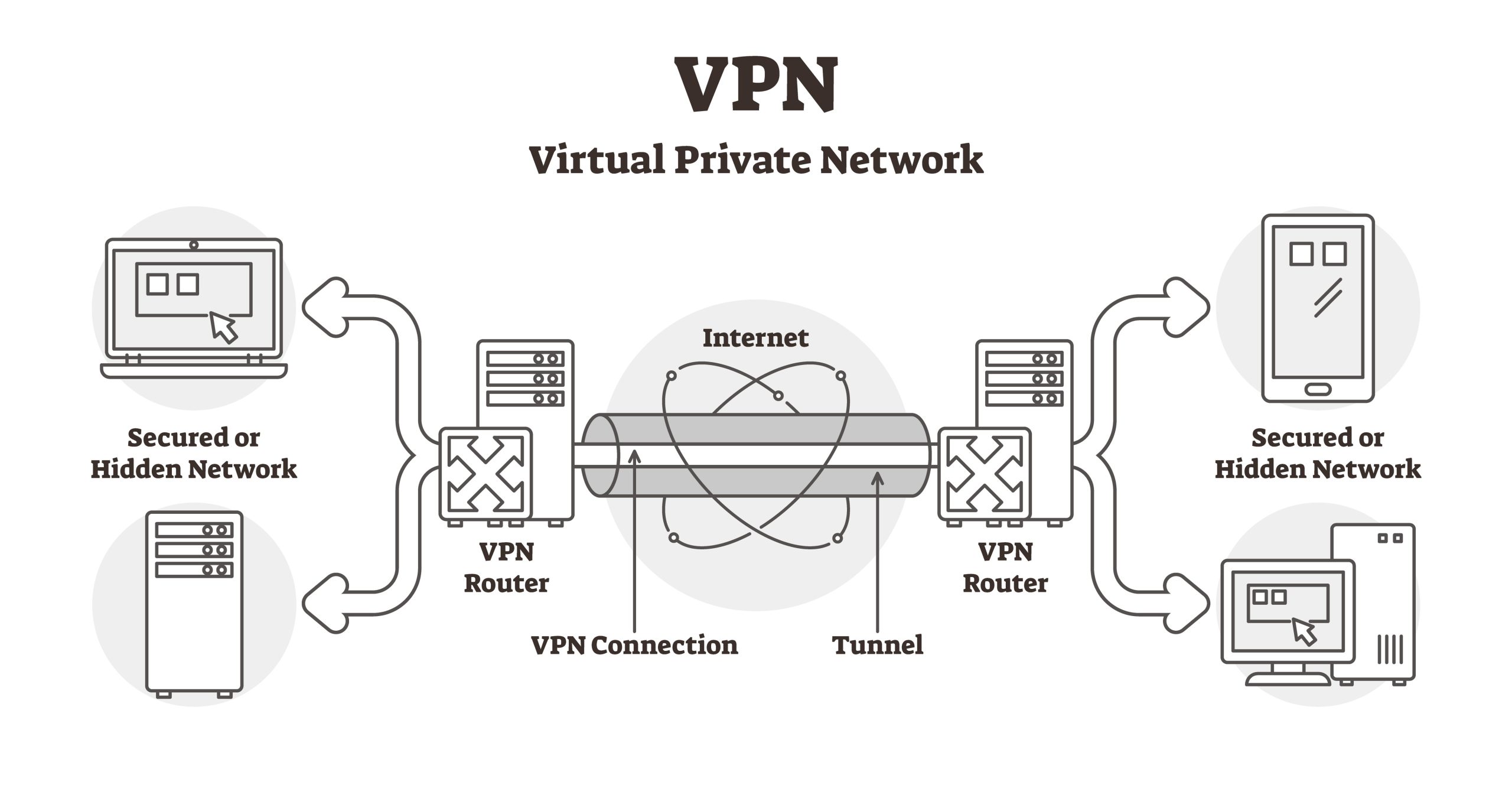
Risk Mitigation Strategies
To protect your business from VPN-related vulnerabilities, consider implementing the following strategies:
- Enhanced Endpoint Security: Ensure all devices connecting to the VPN comply with your security policies. Use mobile device management (MDM) solutions to secure employee devices and implement endpoint detection and response (EDR) solutions. This step is crucial as compromised devices can pose significant security risks to your organization’s VPN.
- Software Update and Patch Management: Regularly update all VPN software and hardware with the latest patches. Automated patch management systems can simplify this process and ensure that your VPN remains protected against newly discovered vulnerabilities.
- User Training and Awareness: Regularly educate employees about VPN security best practices. Conduct training sessions to help them understand the importance of VPN security in protecting sensitive data and responding to potential security threats.
- MFA Implementation: Strengthen user authentication by requiring multiple forms of verification. MFA adds an extra layer of security and reduces the risk of unauthorized access even if login credentials are compromised.
- Regular Security Review: Regularly evaluate your VPN’s security by reviewing configuration settings, user authentication methods, and overall network security. This proactive approach helps identify and address potential vulnerabilities before they can be exploited.
- Reputable VPN Providers: Choose VPN services offering robust encryption, such as Advanced Encryption Standard (AES) 256. Avoid insecure, free, or low-cost options. Consult Managed Service Providers (MSPs) to assess and improve your VPN setup within budget constraints.
Conclusion
VPNs are indispensable for secure remote work and protecting sensitive data. However, they are not immune to vulnerabilities and require regular maintenance and robust security practices. By understanding the vulnerabilities and implementing comprehensive risk mitigation strategies, small businesses can significantly enhance their security posture. Regular security review, strong encryption and endpoint security, MFA implementation, and continuous employee training are essential steps toward safeguarding your business in this constantly evolving digital world.
The NCSS encourages businesses to adopt comprehensive security practices and stay informed about evolving threats. We recommend you consider becoming an NCSS member to access a wide range of our services. For more information, visit our Small Business page.
References
https://www.procheckup.com/blogs/posts/2024/june/vpn-security-audit/
https://nordvpn.com/blog/what-is-pptp-protocol/
https://socradar.io/top-10-vpn-vulnerabilities-2022-h1-2024/
https://sequretek.com/attackers-exploit-vpn-vulnerabilities-in-a-frenzy/
https://thehackernews.com/2024/04/cisco-warns-of-global-surge-in-brute.html
https://thecyberexpress.com/sec-fines-vpn-breach-reporting-delay/
https://www.cybersecuritydive.com/news/check-point-software-hackers-old-vpn/717216/
https://tuxcare.com/blog/cisco-vpn-hijacking-flaw/
https://nationalpost.com/news/canada/global-affairs-vpn-data-breach
https://www.cyber.gc.ca/en/news-events/cyber-activity-impacting-cisco-asa-vpns
https://www.adminbyrequest.com/en/blogs/vpn-vulnerabilities-exposed-rethinking-remote-access
https://www.fortinet.com/resources/cyberglossary/brute-force-attack
https://www.fortinet.com/resources/cyberglossary/man-in-the-middle-attack
https://www.ibm.com/topics/mobile-device-management
https://www.gartner.com/reviews/market/endpoint-detection-and-response-solutions
https://www.pdq.com/blog/what-is-automated-patch-management/

About the NCSS
The National Cybersecurity Society (NCSS) is committed to improving the online safety and security of the small business community through education, awareness, and advocacy. As a 501(3)(c) organization, the NCSS uses funds from charitable donations and grants to develop educational materials, webinars, weekly cyber tips, videos, and how-to-guides. The organization’s goal is to enable and empower small and medium businesses to obtain cybersecurity services, assist them in understanding their cyber risk, and advise on the type of protection needed. We want to continue to grow our community and encourage you to tell other small businesses we are here to help.
The NCSS is committed to respecting the use of images in our communication efforts. Accordingly, unless otherwise specifically noted, the graphics in our bulletin are sourced under license from Adobe Stock. The header and footer images were designed and purchased through a contract with Eyedea Advertising & Design Studio.
